DevOps security is crucial for ensuring the safety and protection of an organization’s systems and data. Secure DevOps practices and the concept of DevSecOps can help organizations maintain a secure and efficient DevOps culture.
Thinking that DevOps and security can exist in silos is a disaster waiting to happen. Many organizations overlook the integration of security in their DevOps culture, leading to severe vulnerabilities. I’ve spent years advocating for and implementing DevSecOps.
DevOps has become a cornerstone for many organizations. However, without security integration, DevOps can leave systems vulnerable. This is where DevSecOps comes into play. DevSecOps, the fusion of development, security, and operations, ensures security is an integral part of the development process. Ignoring this integration can lead to severe consequences.
The Importance of DevOps Security
The Growing Threat Landscape
Cyber threats are evolving. Hackers are becoming more sophisticated. This means traditional security measures are no longer enough. Integrating security into DevOps practices is crucial. It’s not just about protecting data. It’s about ensuring the entire system is resilient against attacks.
Vulnerabilities in Siloed Systems
When DevOps and security exist in silos, gaps appear. These gaps can be exploited by cybercriminals. Many organizations fall into this trap. They treat security as an afterthought. This approach is risky. It leaves systems exposed. By integrating security from the start, these vulnerabilities can be minimized.
The Cost of Data Breaches
Data breaches are expensive. They cost companies millions. Beyond financial loss, there’s reputational damage. Customers lose trust. Recovery takes time. Incorporating security into DevOps can prevent these breaches. It’s an investment in the organization’s future.
What is DevSecOps?
DevSecOps stands for Development, Security, and Operations. It’s about embedding security at every stage of the development process. From planning to coding to deployment. This ensures that security is not an afterthought but a fundamental part of the workflow.
Benefits of DevSecOps

- Proactive Security: Identify and fix vulnerabilities early.
- Continuous Monitoring: Constantly check for threats and weaknesses.
- Better Collaboration: Break down silos between teams.
- Faster Delivery: Secure practices do not slow down development.
- Regulatory Compliance: Ensure adherence to security standards and regulations.
Implementing DevSecOps: Best Practices
The Importance of a Security-First Mindset
Building a security-first mindset is crucial in today’s cyber landscape. In DevSecOps, security isn’t just the responsibility of the security team; it’s everyone’s job. From developers writing code to operations managing infrastructure to management setting policies, everyone must prioritize security.
Steps to Foster a Security Culture
1. Leadership Commitment
Leadership must demonstrate a commitment to security. This involves setting clear security policies, allocating resources for security initiatives, and actively participating in security activities.
Example Code: Security Policy Enforcement
policies:
- name: Password Policy
description: Enforce strong passwords for all user accounts.
rules:
- min_length: 12
- complexity: "uppercase, lowercase, number, special"
- expiration_days: 90
- name: Access Control Policy
description: Define and enforce access controls.
rules:
- role_based_access_control: true
- principle_of_least_privilege: true2. Security Training and Awareness
Regular training sessions help keep security top of mind. Training should cover secure coding practices, common vulnerabilities, and incident response procedures.
Example Code: Training Schedule Automation
schedule:
- name: Monthly Security Training
description: Covering latest security threats and best practices.
frequency: monthly
participants: "all_employees"
- name: Quarterly Incident Response Drills
description: Simulate a security incident to test response capabilities.
frequency: quarterly
participants: "security_team, dev_team, ops_team"3. Regular Workshops and Updates
Organize workshops and updates to keep everyone informed about the latest security threats and practices. These can include guest speakers, hands-on sessions, and interactive activities.
Example Code: Workshop Registration System
import json
# Sample workshop data
workshops = [
{
"title": "Secure Coding Practices",
"date": "2024-07-10",
"instructor": "Jane Doe",
"capacity": 30
},
{
"title": "Understanding OWASP Top 10",
"date": "2024-08-15",
"instructor": "John Smith",
"capacity": 50
}
]
# Function to register for a workshop
def register_for_workshop(user_id, workshop_title):
for workshop in workshops:
if workshop["title"] == workshop_title:
if workshop["capacity"] > 0:
workshop["capacity"] -= 1
print(f"User {user_id} registered for {workshop_title}.")
else:
print(f"Sorry, {workshop_title} is full.")
return
print(f"Workshop {workshop_title} not found.")
# Example usage
register_for_workshop("u12345", "Secure Coding Practices")4. Security Champions Program
Identify and train security champions within each team. These champions act as security advocates, helping to spread best practices and assist in implementing security measures.
Example Code: Security Champions Roster
security_champions:
- name: Alice
team: "Development"
responsibilities:
- conduct code reviews for security
- lead security training sessions for dev team
- name: Bob
team: "Operations"
responsibilities:
- monitor infrastructure security
- manage security incidents and responses5. Incentivize Security Practices
Encourage secure practices by recognizing and rewarding employees who demonstrate exceptional commitment to security. This could include bonuses, awards, or public recognition.
Example Code: Incentive Program Tracker
incentive_program:
- name: Security Star Award
description: Awarded monthly to the employee demonstrating outstanding
security practices.
criteria:
- number_of_security_issues_resolved
- participation_in_security_trainings
- contribution_to_security_projects
- name: Secure Code Bonus
description: Bonus for developers with zero security issues in code reviews.
criteria:
- zero_security_issues_in_code_reviewsBuilding a Security Culture in Practice
Let’s consider a practical scenario. A hypothetical company, TechCorp, decides to build a security-first culture. Here’s how they approached it:
Leadership Commitment
TechCorp’s CEO announced a new security initiative. They allocated a budget for security tools and training. They also appointed a Chief Information Security Officer (CISO) to oversee the implementation.
Security Training and Awareness
TechCorp scheduled monthly security training for all employees. They used interactive online platforms for training modules and quizzes to reinforce learning.
Example Code: Training Platform Integration
training_platform:
name: SecureTrain
integration:
api_key: $SECURETRAIN_API_KEY
training_modules:
- secure_coding: "Secure Coding Practices"
- incident_response: "Incident Response 101"
frequency: monthly
participants: "all_employees"Regular Workshops and Updates
TechCorp held quarterly workshops. They invited industry experts to talk about the latest security trends and threats. Employees participated in hands-on activities to apply what they learned.
Security Champions Program
TechCorp selected security champions from each department. These champions received advanced training and helped their teams adopt secure practices.
Incentivize Security Practices
TechCorp introduced a Security Star Award. Each month, they recognized an employee who went above and beyond in promoting security. This program boosted morale and encouraged everyone to take security seriously.
Example Code: Award Notification System
import smtplib
from email.mime.text import MIMEText
def send_award_notification(winner_email, winner_name):
msg = MIMEText(f"Congratulations {winner_name}! You have been awarded the Security Star Award for this month.")
msg['Subject'] = 'Security Star Award'
msg['From'] = 'security@techcorp.com'
msg['To'] = winner_email
with smtplib.SMTP('smtp.techcorp.com') as server:
server.send_message(msg)
# Example usage
send_award_notification('alice@example.com', 'Alice')Having a security culture, TechCorp (hypothetical company) transformed its approach to security. Employees became more vigilant. Security was integrated into every aspect of their work. This cultural shift laid the foundation for a robust DevSecOps practice.
Creating a security-first culture is an ongoing effort. It requires commitment from everyone in the organization. But the rewards are worth it. A strong security culture leads to fewer vulnerabilities, better compliance, and a more resilient organization.
Automated Security Testing
Automation is a core principle of DevOps. This includes security testing. Automated tests can quickly identify vulnerabilities. Tools like Zed Attack Proxy (ZAP) and Burp Suite are useful.

They integrate with CI/CD pipelines, ensuring security checks at every stage.
Continuous Integration and Continuous Deployment (CI/CD)
CI/CD pipelines streamline development. They ensure quick and efficient deployments. Integrating security checks into these pipelines is essential. This includes static code analysis, dynamic testing, and dependency checks. These automated tests catch issues early, reducing the risk of security breaches.
Example: Secure CI/CD Pipeline
pipeline:
stages:
- name: Build
steps:
- name: Install dependencies
run: npm install
- name: Static Code Analysis
run: npm run lint
- name: Run tests
run: npm test
- name: Security Scan
steps:
- name: Dependency Check
run: npm audit
- name: Dynamic Analysis
run: zap-cli scan http://localhost:3000
- name: Deploy
steps:
- name: Deploy to production
run: deploy.shIntegrate Security Tools
Several tools can help integrate security into DevOps:

- Static Application Security Testing (SAST): Tools like SonarQube.
- Dynamic Application Security Testing (DAST): Tools like Zed Attack Proxy (ZAP) formely callled OWASP ZAP.
- Software Composition Analysis (SCA): Tools like WhiteSource.
These tools automatically scan code and applications for vulnerabilities. They provide immediate feedback, allowing developers to fix issues promptly.
Examples of implementing DevSecOps
Example 1: Financial Services Company
A leading financial services company faced frequent security breaches. These breaches compromised sensitive customer data and damaged their reputation. I was brought in to overhaul their security practices.
Before DevSecOps Implementation
Before adopting DevSecOps, the company’s security practices were fragmented. Security checks were manual and occurred late in the development cycle. This reactive approach left many vulnerabilities undetected until they were exploited.
Issues Identified:
- Manual Security Checks: Time-consuming and inconsistent.
- Late Security Integration: Vulnerabilities discovered too late.
- Siloed Teams: Poor communication between development, operations, and security teams.
DevSecOps Implementation
To address these issues, we integrated security tools into their CI/CD pipeline. This ensured continuous security testing throughout the development process.
Steps Taken:
- Security Culture Shift: Conducted training sessions to instill a security-first mindset.
- Automated Security Testing: Implemented automated security tools for consistent and thorough checks.
- Continuous Monitoring: Established continuous monitoring to detect and respond to threats in real-time.
- Collaboration Tools: Adopted collaboration tools to improve communication between teams.
Code Samples: Integrating Security Tools
1. Static Application Security Testing (SAST) with SonarQube
stages:
- build
- test
- security_scan
- deploy
security_scan:
stage: security_scan
script:
- echo "Starting security scan with SonarQube..."
- sonar-scanner \
-Dsonar.projectKey=FinancialServices \
-Dsonar.sources=. \
-Dsonar.host.url=http://sonarqube:9000 \
-Dsonar.login=$SONAR_TOKEN2. Dependency Checking with OWASP Dependency-Check
security_scan:
stage: security_scan
script:
- echo "Running OWASP Dependency-Check..."
- dependency-check --project "FinancialServices" --scan . --format "ALL" --out
dependency-check-report3. Dynamic Application Security Testing (DAST) with OWASP ZAP
security_scan:
stage: security_scan
script:
- echo "Starting dynamic security scan with OWASP ZAP..."
- zap-cli quick-scan --self-contained http://financialservices.comAfter DevSecOps Implementation
The results were significant. Automated security tests caught vulnerabilities early, reducing the number of breaches. Continuous monitoring provided real-time threat detection. The collaboration between teams improved, leading to faster and more secure deployments.
Outcomes:
- Reduced Vulnerabilities: Early detection and remediation of security issues.
- Faster Deployments: Security integration did not slow down development.
- Enhanced Security Posture: Continuous monitoring ensured ongoing protection.
- Improved Team Collaboration: Break down of silos between teams.
Example 2: E-commerce Platform
An e-commerce platform struggled with regulatory compliance. They were at risk of hefty fines and losing customer trust. Implementing DevSecOps transformed their approach to security and compliance.
Before DevSecOps Implementation
The e-commerce platform’s security was reactive. They performed security checks sporadically, which led to compliance issues and potential data breaches.
Issues Identified:
- Inconsistent Security Checks: Leading to compliance issues.
- Manual Processes: Increased the risk of human error.
- Lack of Real-Time Monitoring: Delayed response to security threats.
DevSecOps Implementation
We embedded security into their development process, ensuring continuous protection and compliance.
Steps Taken:
- Automated Compliance Checks: Integrated tools for automated compliance and security checks.
- Real-Time Monitoring: Implemented real-time security monitoring and alerting systems.
- Training and Awareness: Conducted regular training sessions to maintain a security-focused culture.
Code Samples: Embedding Security Checks
1. Automated Compliance with Chef InSpec
stages:
- build
- test
- security_scan
- compliance_check
- deploy
compliance_check:
stage: compliance_check
script:
- echo "Running compliance checks with Chef InSpec..."
- inspec exec compliance-profile2. Real-Time Monitoring with ELK Stack
monitoring:
stage: monitoring
script:
- echo "Setting up real-time monitoring with ELK Stack..."
- docker-compose -f elk-docker-compose.yml up -d
- echo "Monitoring logs for security events..."
- filebeat -e -c filebeat.yml3. Training and Awareness
stages:
- training
training:
stage: training
script:
- echo "Conducting security training sessions..."
- ./run_security_training.shAfter DevSecOps Implementation
The platform saw a significant improvement in security and compliance. Automated tools ensured continuous protection. Real-time monitoring allowed for quick responses to threats. Regular training maintained a high level of security awareness.
Outcomes:
- Improved Compliance: Automated checks ensured adherence to regulations.
- Enhanced Data Protection: Real-time monitoring reduced the risk of data breaches.
- Increased Customer Trust: Improved security led to higher customer retention.
- Efficient Processes: Automation reduced manual errors and improved efficiency.
These examples highlight the transformative impact of DevSecOps. By integrating security into the development process, organizations can achieve better protection, faster deployments, and greater compliance. Adopting DevSecOps is not just a technical upgrade; it’s a cultural shift that ensures security is everyone’s responsibility.
Overcoming Challenges in DevSecOps Implementation
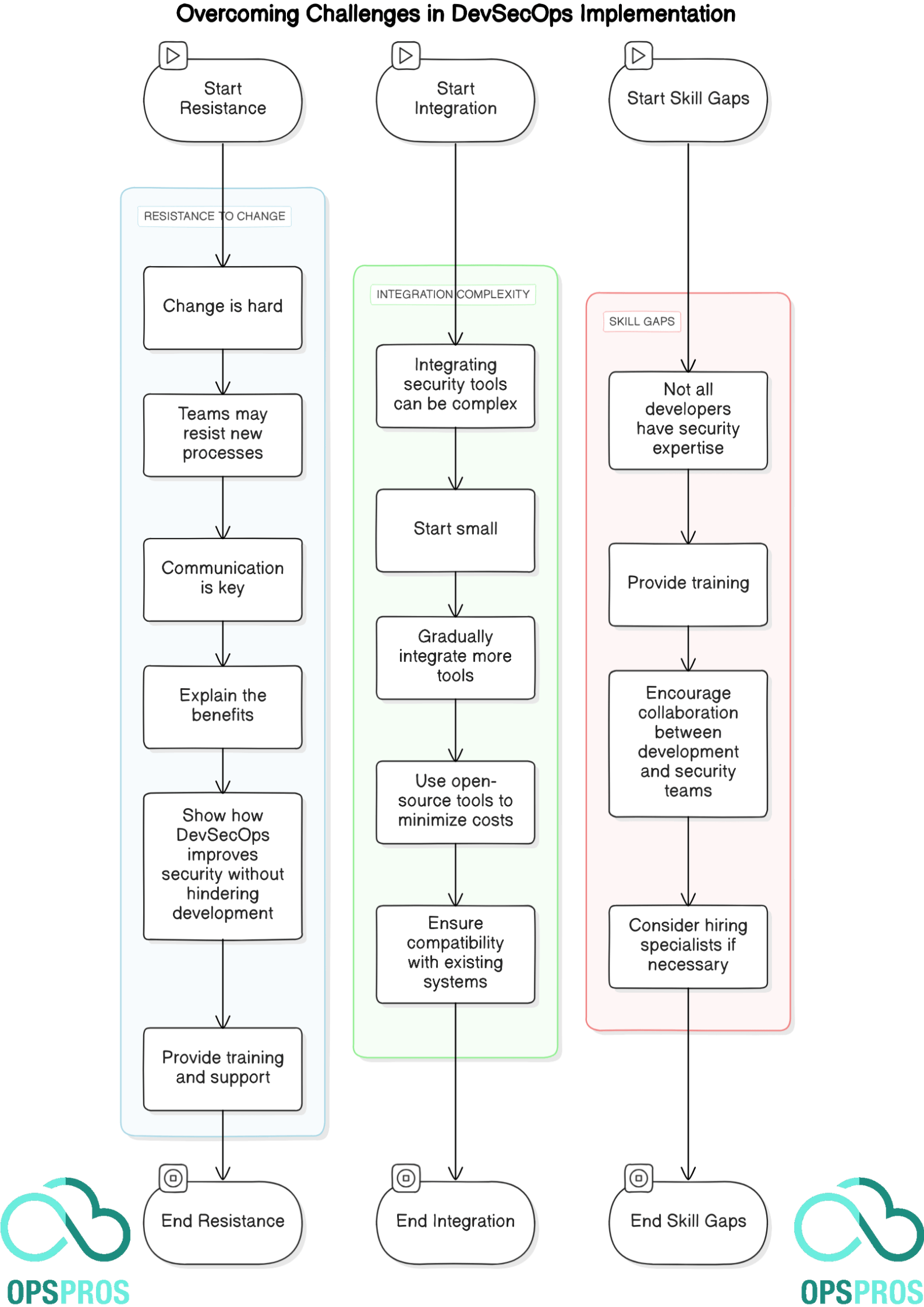
Resistance to Change
Change is hard. Teams may resist new processes. Communication is key. Explain the benefits. Show how DevSecOps improves security without hindering development. Provide training and support.
Integration Complexity
Integrating security tools can be complex. Start small. Gradually integrate more tools. Use open-source tools to minimize costs. Ensure compatibility with existing systems.
Skill Gaps
Not all developers have security expertise. Provide training. Encourage collaboration between development and security teams. Consider hiring specialists if necessary.
Final Thoughts

Security is crucial in today’s digital landscape. DevOps practices must evolve to include security. DevSecOps is the solution. It integrates security into every stage of development. This proactive approach reduces vulnerabilities and protects data. Organizations that embrace DevSecOps will be better equipped to face modern cyber threats.
Noah is an accomplished technical author specializing in Operations and DevOps, driven by a passion ignited during his tenure at eBay in 2000. With over two decades of experience, Noah shares his transformative knowledge and insights with the community.
Residing in a charming London townhouse, he finds inspiration in the vibrant energy of the city. From his cozy writing den, overlooking bustling streets, Noah immerses himself in the evolving landscape of software development, operations, and technology. Noah’s impressive professional journey includes key roles at IBM and Microsoft, enriching his understanding of software development and operations.
Driven by insatiable curiosity, Noah stays at the forefront of technological advancements, exploring emerging trends in Operations and DevOps. Through engaging publications, he empowers professionals to navigate the complexities of development operations with confidence.
With experience, passion, and a commitment to excellence, Noah is a trusted voice in the Operations and DevOps community. Dedicated to unlocking the potential of this dynamic field, he inspires others to embrace its transformative power.